">
DisacoEndpoint Security
What Is Endpoint Security?
Endpoint security is the practice of securing endpoints or entry points of end-user devices such as desktops, laptops, and mobile devices from being exploited by malicious actors and campaigns. Endpoint security systems protect these endpoints on a network or in the cloud from cybersecurity threats. Endpoint security has evolved from traditional antivirus software to providing comprehensive protection from sophisticated malware and evolving zero-day threats.
Organizations of all sizes are at risk from nation-states, hacktivists, organized crime, and malicious and accidental insider threats. Endpoint security is often seen as cybersecurity’s frontline, and represents one of the first places organizations look to secure their enterprise networks.
As the volume and sophistication of cybersecurity threats have steadily grown, so has the need for more advanced endpoint security solutions. Today’s endpoint protection systems are designed to quickly detect, analyze, block, and contain attacks in progress. To do this, they need to collaborate with each other and with other security technologies to give administrators visibility into advanced threats to speed detection and remediation response times.

Why endpoint security is important?
An endpoint protection platform is a vital part of enterprise cybersecurity for a number of reasons. First of all, in today’s business world, data is often the most valuable asset a company has—and to lose that data, or access to that data, could put the entire business at risk of insolvency. Businesses have also had to contend with not only a growing number of endpoints, but also a rise in the number of types of endpoints. These factors make enterprise endpoint security more difficult on their own, but they’re compounded by remote work and BYOD policies—which make perimeter security increasingly insufficient and create vulnerabilities. The threat landscape is becoming more complicated, too: Hackers are always coming up with new ways to gain access, steal information or manipulate employees into giving out sensitive information. Add in the opportunity cost of reallocating resources from business goals to addressing threats, the reputational cost of a large-scale breach, and the actual financial cost of compliance violations, and it’s easy to see why endpoint protection platforms have become regarded as must-haves in terms of securing modern enterprises.


Endpoint security components
Typically, endpoint security software will include these key components:
- Machine-learning classification to detect zero-day threats in near real-time
- Advanced anti-malware and antivirus protection to protect, detect, and correct malware across multiple endpoint devices and operating systems
- Proactive web security to ensure safe browsing on the web
- Data classification and data loss prevention to prevent data loss and exfiltration
- Integrated firewall to block hostile network attacks
- Email gateway to block phishing and social engineering attempts targeting your employees
- Actionable threat forensics to allow administrators to quickly isolate infections
- Insider threat protection to safeguard against unintentional and malicious actions
- Centralized endpoint management platform to improve visibility and simplify operations
- Endpoint, email and disk encryption to prevent data exfiltration
Advanced endpoint security solutions
McAfee offers a full range of solutions that combine powerful endpoint protection with efficient endpoint management. McAfee Endpoint Security combines established capabilities such as firewall, reputation, and heuristics with cutting-edge machine learning and containment, along with endpoint detection and response (EDR) into a single platform agent, with a single management console. The resulting integrated endpoint protection platform keeps users productive and connected while stopping zero-day malware, like ransomware, before it can infect the first endpoint.
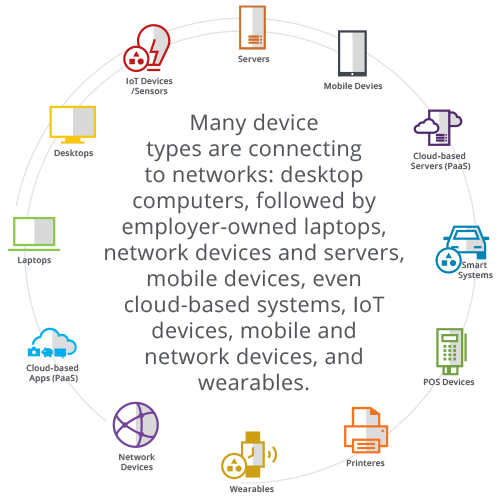
What’s considered an endpoint?
Endpoints can range from the more commonly thought of devices such as:
- Laptops
- Tablets
- Mobile devices
- Smart watches
- Printers
- Servers
- ATM machines
- Medical devices
Contact us
Response 7/24 hours a day
Contact us
Response 7/24 hours a day
If you have any questions or queries a member of staff will always be happy to help. Feel free to contact us by telephone or email and we will be sure to get back to you as soon as possible.